Watch the Long Play version at Debian Wheezy 2015-01-31 3.18You only have to do this if using.Wheezy.There be no need to. Any and all resources related to metasploit on this wiki MSF - on the metasploit framework generally. Category:Metasploit - pages labeled with the 'Metasploit' category label. MSF/Wordlists - wordlists that come bundled with Metasploit. MSFVenom - msfvenom is used to craft payloads. Meterpreter - the shell you'll have when you use MSF to craft a remote shell payload. OpenSSH runs as two processes when connecting to other computers. The first process is a privileged process and controls the issuance of privileges as. Openssh-6.7 free download. Some styles failed to load. 😵 Please try reloading this page.
Last updated on MARCH 31, 2020
Applies to:
Oracle Database - Standard Edition - Version 11.2.0.4 and laterOracle Database Backup Service - Version N/A and later
Openssh 6.7p1 Exploit
Oracle Database Cloud Service - Version N/A and laterOracle Database Cloud Schema Service - Version N/A and later
 Oracle Cloud Infrastructure - Database Service - Version N/A and later
Oracle Cloud Infrastructure - Database Service - Version N/A and laterOpenssh For Windows 10
Linux x86-64
OpenSSH version 6.7 installed on one or more nodes
Openssh 6.7p1
Symptoms
SSH connectivity fails during installation of 12.1.0.2 Grid Infrastructure despite being able to successfully ssh to each node through a shell.
installActions<time_stamp>.log shows the following:
Openssh Upgrade Centos 7
Additionally, the sshsetup<time_stamp>.log will show:
SEVERE: com.jcraft.jsch.JSchException: Algorithm negotiation fail <---HERE
at com.jcraft.jsch.Session.receive_kexinit(Session.java:529)
at com.jcraft.jsch.Session.connect(Session.java:291)
at com.jcraft.jsch.Session.connect(Session.java:154)
at oracle.sysman.prov.ssh.RunCommand.runCommand(RunCommand.java:195)
at oracle.sysman.prov.ssh.SSHSetup.runCommandHelper(SSHSetup.java:2370)
at oracle.sysman.prov.ssh.SSHSetup.validateRemoteBinaries(SSHSetup.java:2597)
at oracle.sysman.prov.ssh.SSHSetup.validateRemoteHosts(SSHSetup.java:1194)
at oracle.sysman.prov.ssh.SSHSetup.setupConnectivity(SSHSetup.java:775)
at oracle.install.driver.oui.OUISSHSupportManager.establishSSHConnectivity(OUISSHSupportManager.java:170)
at oracle.install.ivw.common.view.SSHSetupPane$7.perform(SSHSetupPane.java:288)
at oracle.install.ivw.common.view.SSHSetupPane$SSHOperation.run(SSHSetupPane.java:347)
Changes
OpenSSH 6.7 is installed or was upgraded prior to start OUI:
OpenSSH_6.7p1 (CentrifyDC build 5.2.3-425) , OpenSSL 0.9.8zf-fips 19 Mar 2015
Cause
To view full details, sign in with your My Oracle Support account. |
Don't have a My Oracle Support account? Click to get started! |
| Symptoms |
| Changes |
Openssh 6.7 Vulnerability
| Cause |
| Solution |
| References |
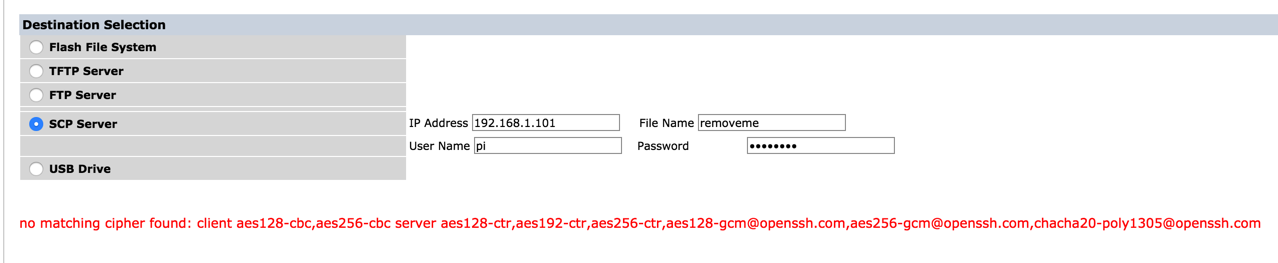
For those using ssh over rsync or just scp to move files around on a LAN, be aware that a number of version 2 ciphers have been disabled in the 6.7p1-1 release of openssh (see release notes) including the following:
3des-cbc
blowfish-cbc
cast128-cbc
arcfour
arcfour128
arcfour256
aes128-cbc
aes192-cbc
aes256-cbc
rijndael-cbc@lysator.liu.se
That leaves the following available:
aes128-ctr
aes192-ctr
aes256-ctr
aes128-gcm@openssh.com
aes256-gcm@openssh.com
chacha20-poly1305@openssh.com
If you have defined any of these ciphers in ~/.ssh/config you should switch to one of the supported ones. Also make the change in any shell script you might be using. The significance of this particularly for older hardware could be much slower transfer speeds. See this thread for a comparison of all version 2 ciphers moving 500 MB files around. The conclusion from this older experiment was that any of the arcfour ciphers provided the fastest transfers on LANs where security was not a concern.
Using a similar script I shared in the linked thread, I tested these supported ciphers an 1100 MB file this time (with 6 replicates) and found that all are more or less the same within error of the experiment on the Ivy or Haswell hardware tested (with the exception of the chacha20-poly1305 cipher that was a tiny bit slower on each). The older Yorkfield (Xeon version of the Q9550) had a harder time keeping up and slightly preferred the aes256-gcm cipher. YMMV.
Openssh Upgrade
Openssh 6.7p1 Vulnerabilities
None of these were CPU-limited using my hardware (sending machine was a Haswell i7-4790k and receiving machines are as indicated in the headers on the plots.
You can benchmark your own hardware with the script below:
Script: https://gist.github.com/graysky2/0e265604bfd4856a2596
Last edited by graysky (2015-11-22 22:16:24)
