- See All Results For This Question
- Sophos Anti-Virus For Linux: Locally Compiling Talpa Binary ...
- Cached
- Sophos Talpa とは
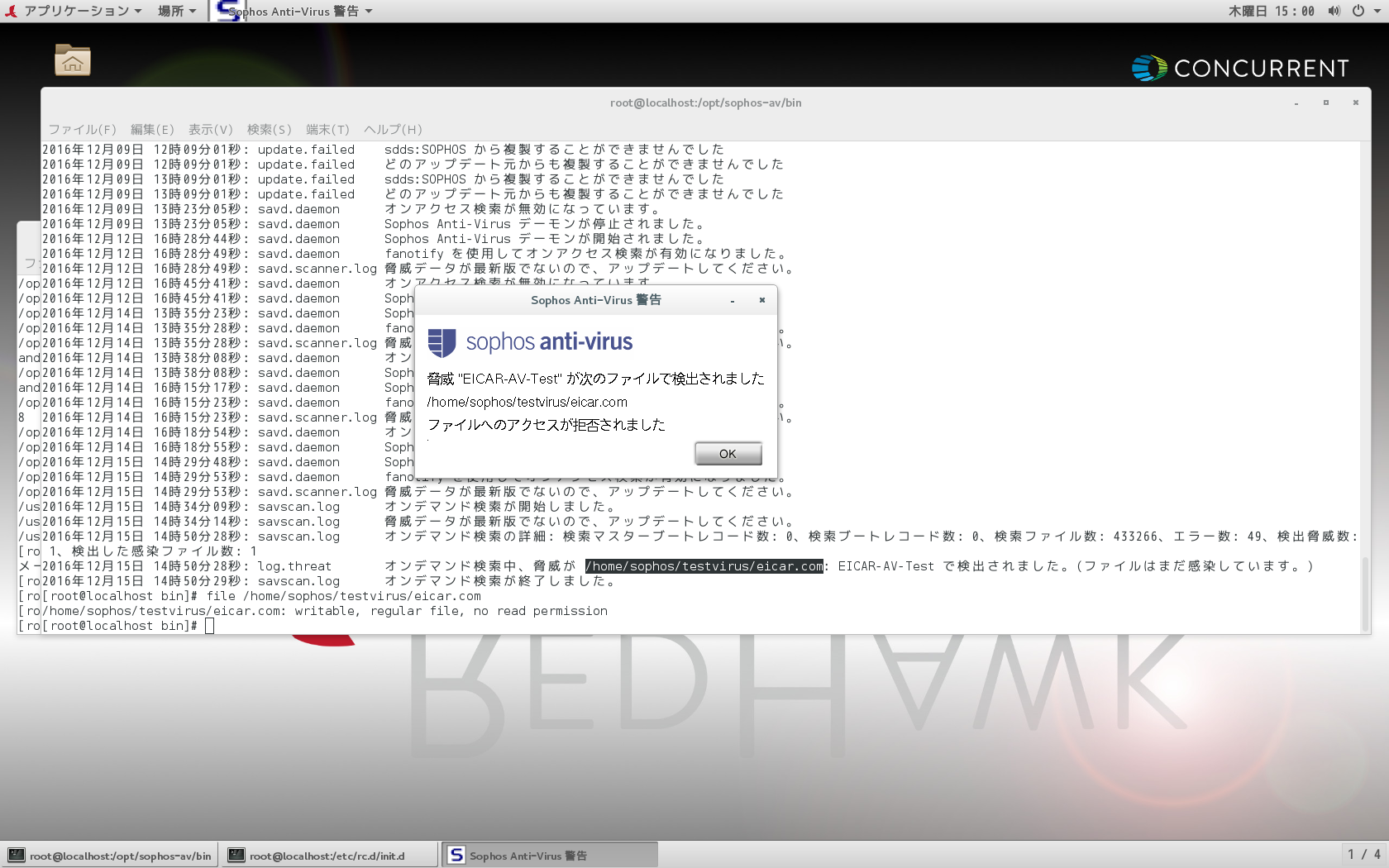
For Sophos Antivirus for Linux to detect threats in Docker containers, the Talpa on-access driver must be used. The FAnotify kernel interface does not support scanning inside containers. A recent, supported version of Docker will need to be installed and configured, preferably from the operating system vendor’s package repositories. Overview Sophos does not provide Talpa Binary Packs (TBPs) for all Linux kernels. This knowledge base article contains the steps on how to install the necessary prerequisites and create TBPs for other kernels, without the need to install additional tools on each computer. Sophos Anti-Virus for Linux: Talpa Binary Pack update is triggered when a new Binary Pack is required after a Linux kernel update Sign up to the Sophos Support SMS Notification Service to get the latest product release information and critical issues.
This article details the addition of support for Docker containers within Sophos Antivirus for Linux.
The following sections are covered:
Applies to the following Sophos products and versions
Sophos Anti-Virus for Linux
As containers are becoming more widely deployed on Linux Servers, the need for security is paramount to ensure any running containers have not been injected with malware.
Sophos Antivirus for Linux has been enhanced to improve detection of malware in Docker containers using on-access scanning and to improve the way in which detections in Docker containers are presented within the Sophos management consoles. Now, when a threat is identified within a Docker container, the threat report will state the path and hostname of the container. This will be displayed as (container hostname=<hostname>).
Threat detection within Docker containers has been available since the following versions of Sophos Antivirus for Linux:

- SAV for Linux version 9.13.0+
- SAV for Linux version 10.1.1+ (Sophos Central only)
For Sophos Antivirus for Linux to detect threats in Docker containers, the Talpa on-access driver must be used. The FAnotify kernel interface does not support scanning inside containers.
A recent, supported version of Docker will need to be installed and configured, preferably from the operating system vendor’s package repositories.
The Sophos Antivirus for Linux Docker scanning functionality is available on Supported releases of the following platforms:
See All Results For This Question

Red Hat, Ubuntu, CentOS, SUSE
Sophos Anti-Virus For Linux: Locally Compiling Talpa Binary ...
For more information on Sophos Anti-virus for Linux see: supported platforms and operating systems
From the Docker web site, the following anti-virus consideration is recommended:
When antivirus software scans files used by Docker, these files may be locked in a way that causes Docker commands to hang.
One way to reduce these problems is to add the Docker data directory (/var/lib/docker on Linux or $Env:ProgramData on Windows Server) to the antivirus’s exclusion list. However, this comes with the trade-off that viruses or malware in Docker images, writable layers of containers, or volumes are not detected. If you do choose to exclude Docker’s data directory from background virus scanning, you may want to schedule a recurring task that stops Docker, scans the data directory, and restarts Docker.
If you’ve spotted an error or would like to provide feedback on this article, please use the section below to rate and comment on the article.
This is invaluable to us to ensure that we continually strive to give our customers the best information possible.
Related:
| #!/bin/bash |
| set -o pipefail |
| [[ -n'$WORKING_DIR' ]] || WORKING_DIR='$1' |
| [[ -n'$WORKING_DIR' ]] || WORKING_DIR=$(pwd) |
| functionfailure() |
| { |
| echo'$@' |
| exit 2 |
| } |
| mkdir -p '$WORKING_DIR'|| failure 'Unable to create working directory $WORKING_DIR: $?' |
| cd'$WORKING_DIR' |
| functiongitupdate() |
| { |
| git pull 2>&1| tee git.log || failure 'Unable to pull with git' |
| grep 'Already up-to-date.' git.log >/dev/null |
| } |
| functionp4update() |
| { |
| P4=p4 |
| [[ -x /opt/perforce/bin/p4 ]] && P4=/opt/perforce/bin/p4 |
| '$P4' sync 2>&1| tee perforce.log || failure 'Unable to sync to perforce' |
| grep 'File(s) up-to-date' perforce.log >/dev/null |
| } |
| [[ -f configure ]] || FORCE=1 |
| [[ -f .p4options ]] && P4CONFIG=.p4options |
| [[ -f P4CONFIG ]] && P4CONFIG=P4CONFIG |
| [[ -f .p4config ]] && P4CONFIG=.p4config |
| if [[ -d .git ]] |
| then |
| gitupdate && { [[ $FORCE-eq 1 ]] ||exit 77 ; } |
| elif [[ -n'${P4CONFIG}' ]] |
| then |
| export P4CONFIG |
| p4update && { [[ $FORCE-eq 1 ]] ||exit 77 ; } |
| else |
| git clone https://github.com/sophos/talpa.git . -b perforce --depth 20 || failure 'Unable to clone git repository' |
| fi |
| ## Got an update |
| [[ -f configure ]] || ./bootstrap || failure 'Unable to bootstrap' |
| [[ -f makefile ]] || ./configure --disable-talpa-build --enable-maintainer-mode || failure 'Unable to configure' |
| make talpa-srcpack.tar.gz || failure 'Unable to build Talpa srcpack' |
| [[ -n'$INST' ]] || INST=/opt/sophos-av |
| if [[ -d'$INST' ]] |
| then |
| cp -v talpa-srcpack.tar.gz $INST/talpa/override/ || failure 'Unable to copy talpa-srcpack.tar.gz to $INST/talpa/override/' |
| $INST/engine/talpa_select select|| failure 'Unable to do talpa_select select' |
| $INST/bin/savdctl disable || failure 'Unable to disable on-access' |
| sleep 2 |
| $INST/bin/savdctl enable|| failure 'Unable to enable on-access' |
| fi |
| exit 0 |
Cached
commented Sep 15, 2016
To use this, download the script to e.g. /root/autodeploy.sh Then run /bin/bash /root/autodeploy.sh /root/talpa Then add to crontab e.g.: |
commented Dec 2, 2018
Thanks, worked perfectly. Now I have 'Talpa' on a new kernel. |
Sophos Talpa とは
